 Wee
Siong Ng (Ph.D)
Wee
Siong Ng (Ph.D)| [1] Fuzzy Linking of trajectories Datasets for Identity Discovery.
Mingqiang Xue, Huayu Wu & Wee Siong Ng [Patent Application No: 10201401124X (Pending)] |
|
Nowadays, digital devices and services are widely used by citizens in most modern cities. For example, tele-communication and social network services on the Internet are replacing letters, surveillance cameras are replacing human guards, smart cards are replacing paper tickets for public transport, credit cards are replacing cash payments, etc. All the systems and devices supporting the abovementioned services are collecting very rich information about people’s trajectories every day. Telco companies maintain CDR data about every user, including where and when he/she makes a call; original-destination of commuters can be extracted from transportation smart card; banks and credit card companies record all the transactions for each customers about the time and location he/she makes the payment; social network service providers keep the check-in information of users, and so on and so forth.
Due to the fact that most people use more than one services and thus expose their trajectories to different service providers, linking up all the trajectories for the same person, which are kept in various sources, would greatly enrich the knowledge on the citizens’ movement and help to solve many practical urban problems. We use two examples to illustrate.
Example 1. The healthcare authority is keen to control the spread of serious infectious diseases, such as SARS. If a particular taxi driver is infected, the authority would like to know who are the passengers that were served by this taxi in the last two days, so that isolation and monitoring operations can be taken onto those passengers. On one hand, the taxi company records the trajectories of the taxi and knows the places and times that the taxi picked up and dropped off a passenger, however, it cannot know the identity of each passenger. On the other hand, the telco company maintains the CDR data that traces every customer even if he/she is not making a call (the cell phone keeps communicating with the cell tower all the time). If it is possible to match the trajectory of a passenger in the taxi to the CDR trajectory of a particular phone number, we will know the passenger’s phone number and probably his/her identity as most telco companies require real-name registration for the mobile service. Example 2. Suppose violence happens inside the subway system station and the suspect was caught on the surveillance camera tapping his card in the exit gate at 13:51. From the transportation smart card records, the card number of the person (or a limited number of candidates) can be found out and so does his whole public transport trajectories. By linking up his public transport trajectories to the CDR trajectories, we may be able to find the phone number and other information of the suspect. As illustrated, linking up two or more trajectories of a person can help to gain richer insight of the person’s movement. Furthermore, linking up anonymous trajectories with real name trajectories will help to re-identify the person with the anonymous movements. In our technology, we invent algorithms to link different trajectories that belong to the same person. Different from other data integration technologies, which focus on matching two or more data sources with the same content textually or semantically, our algorithm takes probabilistic model to discover the two trajectories that belong to the same person, even though the two trajectories do not share any common data points. Our technology can be used by public and private organizations that have access to the multiple trajectory data sources, to solve different urban problems as demonstrated above, or to provide better social services. |
|
|
| [2] Advanced Data Exchange Platform.
Huafei Zhu & Wee Siong Ng [Patent Application No: 10201406821R (Pending)] |
|
A data exchange platform benefits users to collect, share,
process, update and outsource their personal data and brings
commercial values to the users. The most challenging aspect
of the data exchange lies in supporting of the keyword search
so that the common interested data can be processed and
exchanged over the platform securely and efficiently. In this
patent, a systematic approach for designing multi-key searchable
encryption is proposed and analyzed. Our design aims
for a scale and sustainable system built open and adaptable.
When the deployed processing nodes are individually unreliable,
as is the case in modern data centers, redundancy must
be introduced into the system to improve reliability against
node failures. The system is employing the threshold secret
key sharing technique to provide high reliability with limited
storage overhead. The proposed search engine is constructed
from a hybrid of the Hellman-Pohlig function and the ElGamal
encryption scheme defined over
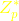 and it achieves the
semantic security (the user anonymity, the keyword hiding,
the token hiding and the data hiding) assuming that the
decisional Diffie-Hellman problem is hard over and it achieves the
semantic security (the user anonymity, the keyword hiding,
the token hiding and the data hiding) assuming that the
decisional Diffie-Hellman problem is hard over 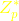 . To the
best of our knowledge, this is the first multi-key searchable
encryption defined over . To the
best of our knowledge, this is the first multi-key searchable
encryption defined over 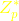 . .
|
|
|